
What are malicious usb keys and how to create a realistic one?
This blog post shows how to create a reliable and realistic-looking malicious USB key that can be used in a drop attack.

How 'Juice Jackers' Plant Malware On Your Phone At Airports And Hotels

Explained: juice jacking

What are malicious usb keys and how to create a realistic one?

Malicious USB devices: What are the risks?
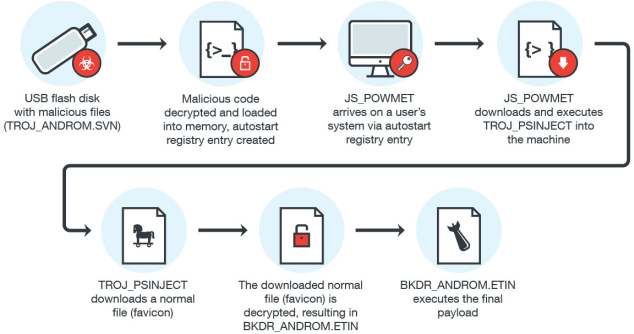
USB Malware Implicated in Fileless Attacks

Malicious USB devices: Still a security problem
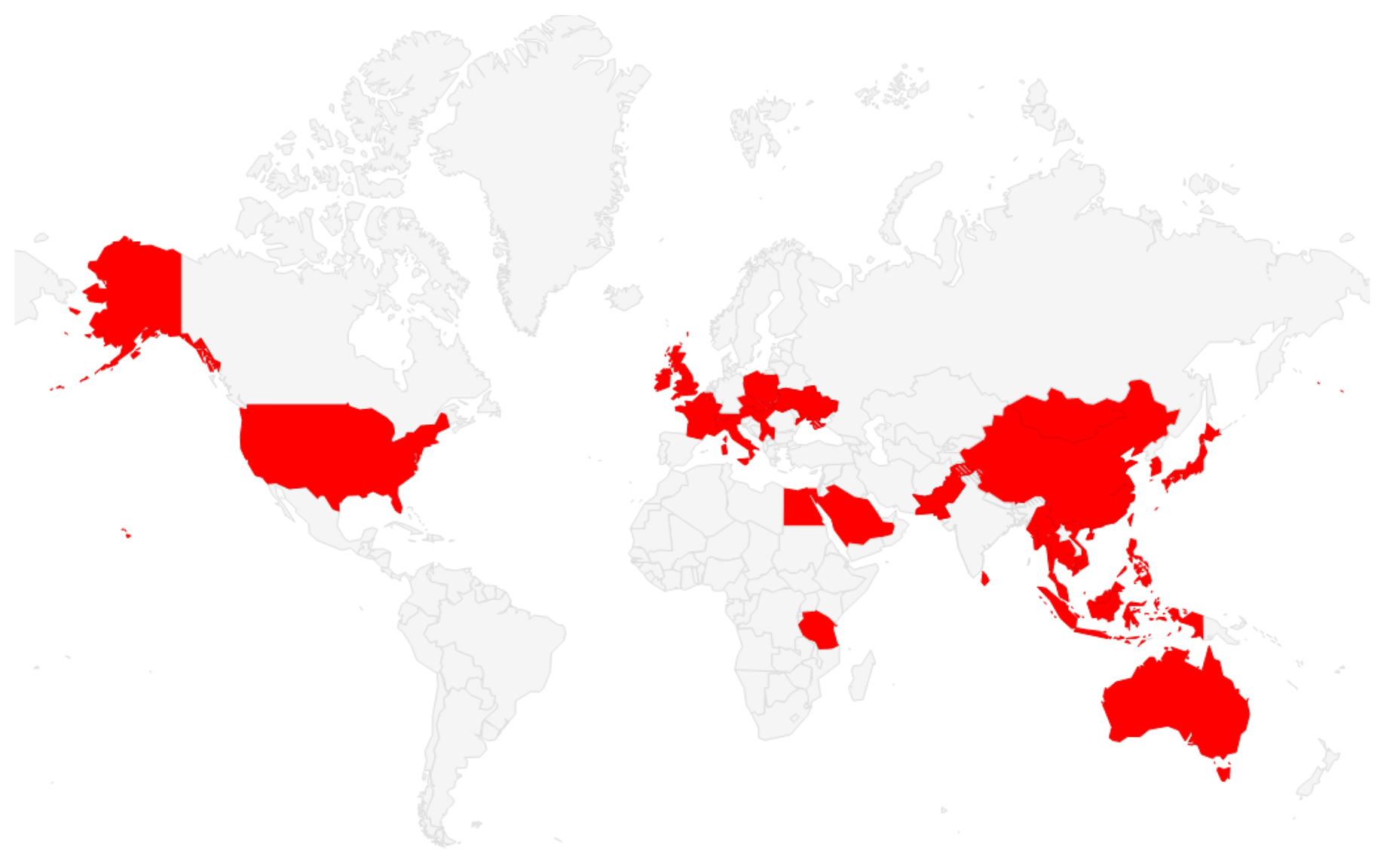
The Spies Who Loved You: Infected USB Drives to Steal Secrets
DESCRIPTION Flexible Silicone Replacement Sleeve For Aegis Secure Key 3NX/3NXC and Aegis Secure Key 3z only Not compatible with Aegis Secure Key 3.0

Protective Sleeve Aegis Secure Key 3NX/3Z

Transforming USB sticks into undetectable malicious devices
Beware Random USB Sticks - Daily Security Byte - Secplicity









